| "Creativity is thinking up new things. Innovation is doing new things." Theodore Levitt
|
|
 |
Welcome to
iAccess project! |
|
iAccess Negotiation-based Authorization Service
*** iAccess v2.0 beta already available for download. ***
Next release will include the source code, some examples and improvements. Scheduled soon.
|
|
|
iAccess project initially started with the efforts of Hristo Koshutanski, Fabio Massacci and Aliaksandr Lazouski with release v1.1.
The project has been successfully moved to a new level of design and functionality
thanks to the support by Safe Society Labs, S.L. and the efforts of Hristo Koshutanski, Antonio Maña and Ernesto José Pérez García, and made available to you with release v2.0.
The new iAccess architecture aims at enhancing web services security by trust negotiation based access control. The new iAccess software undergone a major redesign and implementation (from scratch) of all components to meet the criteria of the European Project OKKAM where it has been integrated as part of the project's Entity Name System.
iAccess integrates state-of-the-art web services security standards implementation and provides secure and trusted interactions between information systems. It realizes the notion of security proxy as a way to facilitate easy deployment in information systems.
New features include:
- Improved trust negotiation protocol.
- Enabled two modes of negotiation: brave and cautious modes.
- Improved certificate handling in security policies.
- Network firewall and http load balancer traversal.
- Complete integration with Metro high-performace WS-* stack component.
- Replication of iAccess negotiation service inside a cluster of machines. This feature requires memcached service availability.
|
|
|
iAccess software Copyright © 2010 by Ernesto José Pérez García and Hristo Koshutanski.
iAccess authorization service software (called iAccess) is free software: you
can redistribute it and/or modify it under the terms of the GNU Lesser General
Public License as published by the Free Software Foundation, either version 3 of
the License, or (at your option) any later version.
iAccess is distributed in the hope that it will be useful,
but WITHOUT ANY WARRANTY; without even the implied warranty of
MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU Lesser General Public License for details.
|
|
|
Binary distribution of software is already available for download. Next iAccess release will include source code and examples of usage.
There are two packages - client and server parts, released with already configured security policies and X.509 (identity and attribute) certificates. The two packages include also the Metro libraries and the DLV system binaries. Each zip package contains all necessary data for the iAccess proxy to function.
Download and install the two packages (in different folders if one machine). Installing an iAccess component is unzipping the downloaded file into a location (a folder) of your choice. We name the full path to that location as PROXY_ROOT. Run PROXY_ROOT/okkam-proxy.exe if Windows OS, or PROXY_ROOT/okkam-proxy.sh if Unix OS. The iAccess proxy requires Java 6 installed on your machine.
|
|
|
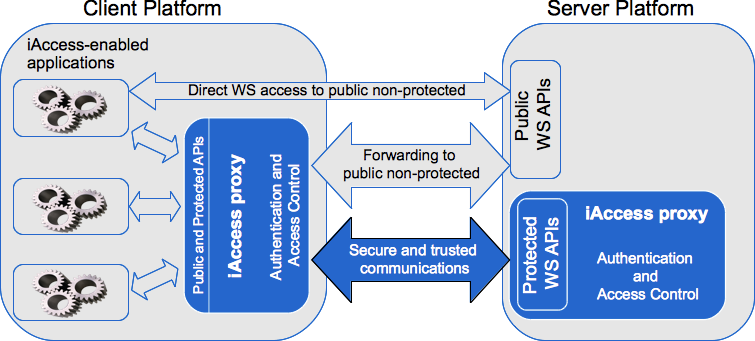
Figure 1: iAccess proxy communications API-level
There are two main functional modes: client-side and server-side. The client-side iAccess proxy can be used as a Java library or as a local host service. The local host service mode targets so called thin applications which are unable to use iAccess as a java library.
WS applications instead of connecting to a remote WS API they invoke to the local iAccess proxy APIs, which in turn handles authorization with the remote server (its corresponding iAccess proxy). Upon successful authorization (authentication, access control and secure channel establishment) the client-side proxy invokes the remote API and forwards the response back to the (local) application.
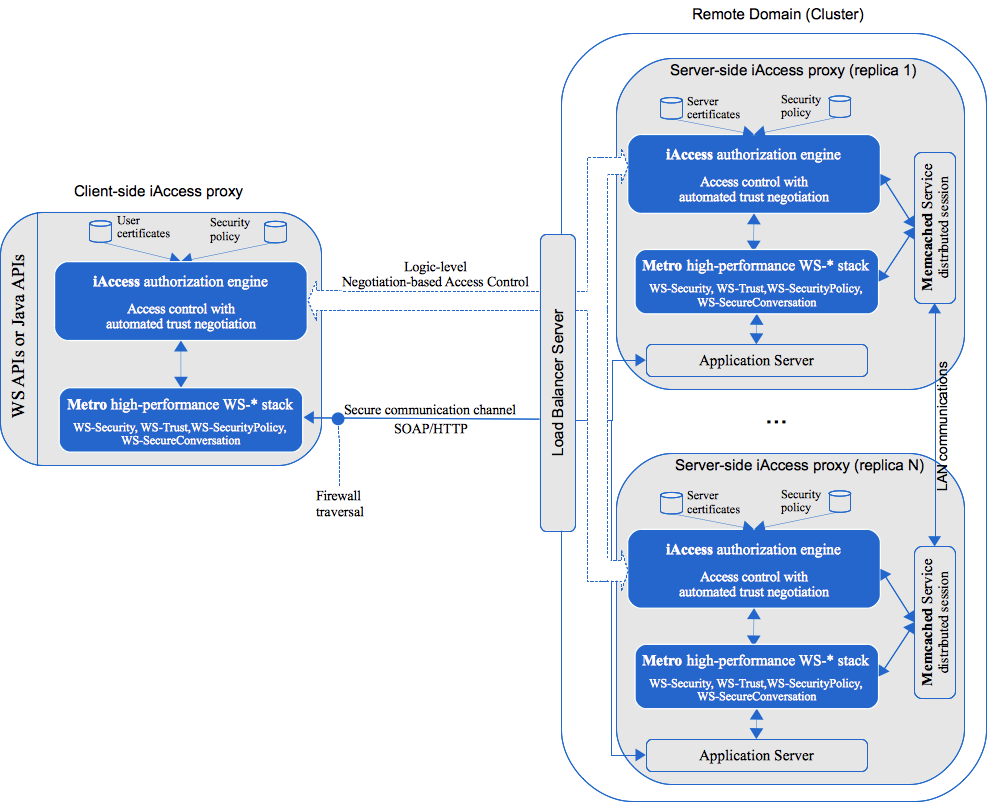
Figure 2: iAccess proxy architecture and communications inside view
|
|
|
Should you have any questions/recommendation/feedback regarding the project, software, and the source code release please contact Hristo Koshutanski.
People contributed to the project:
|
|